LDAP User Import with Groups in Liferay 7 / DXP
April 28, 2022
Directory Services store information in organized manner usually in hierarchical structure. LDAP Servers are commonly used to store usernames, passwords and can be connected by using LDAP Protocol that is based on TCP/UDP.
Since LDAP Servers are central places for information storage, many of the times we require to fetch user specific information from them at the time of login (for validation), system start up or at the regular time intervals.
In this Post, we will see step by step how we can validate an user against LDAP and import details of user and groups that user is associated to (in LDAP) and create the link between them (for which user is assigned a role that is created in liferay for a Group) into Liferay.
Here we will be referring the Liferay version 7.0 but the steps provided are mostly generic across all versions.
In Liferay 7 LDAP configuration has to be done from Control Panel > Configuration > Instance Settings.
Scroll down to Authentication section and select LDAP from tab sequence as shown below.
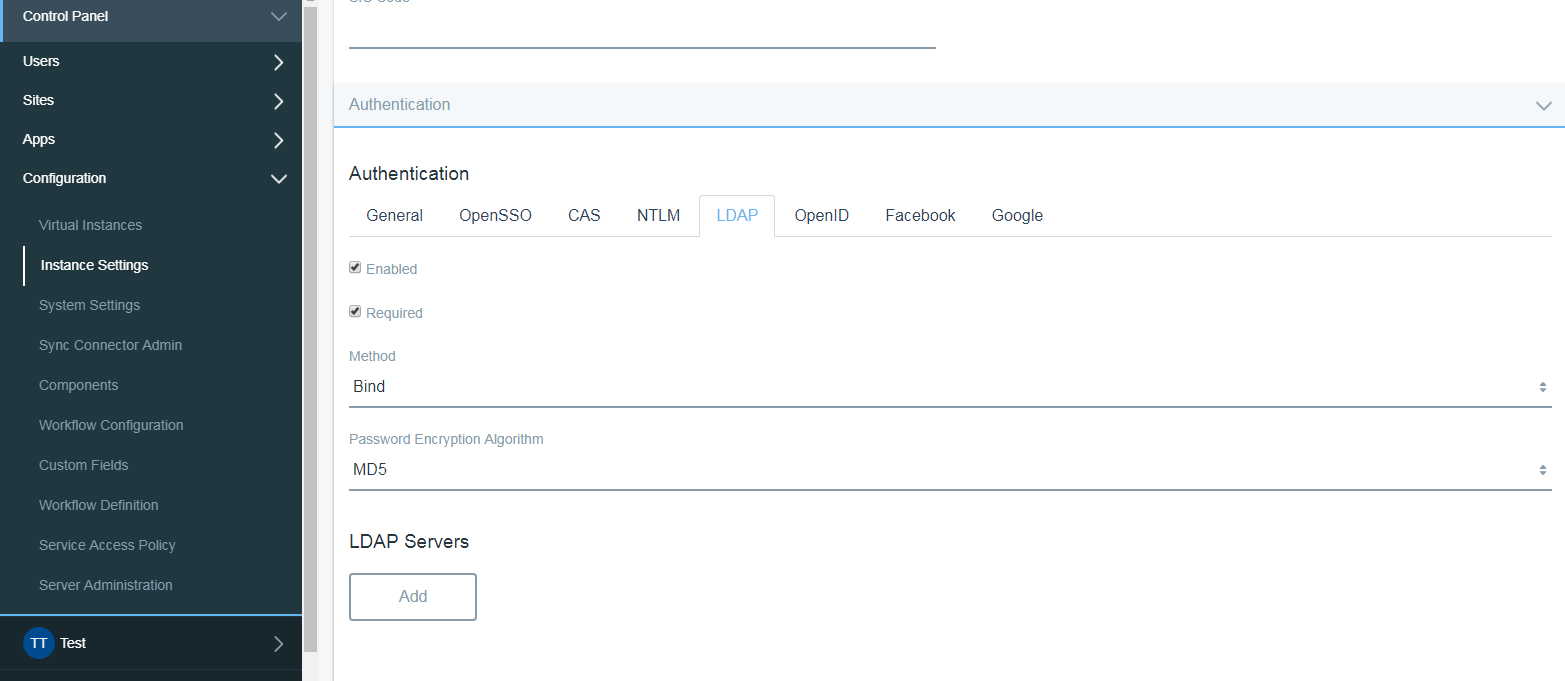
Let’s add an LDAP server first for which click on Add button under Label LDAP Servers.
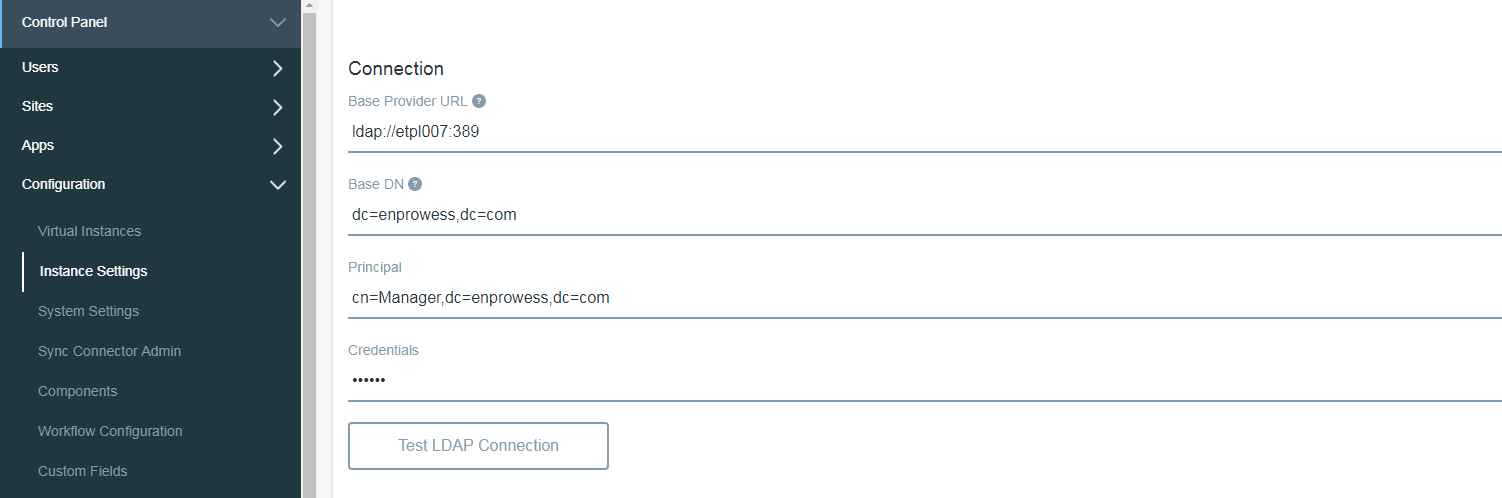
Provide basic connection details as below and Click on Test LDAP Connection.
- Note :- I am using OpenLDAP as an LDAP Implementation tool but there is no restriction on using other products such as Apache DS, OpenDJ etc..
It should show a message in Popup as below upon successfully connecting to LDAP Server. Once a connection to LDAP is successfully established, fill in the details of User attributes that define details about user in LDAP.
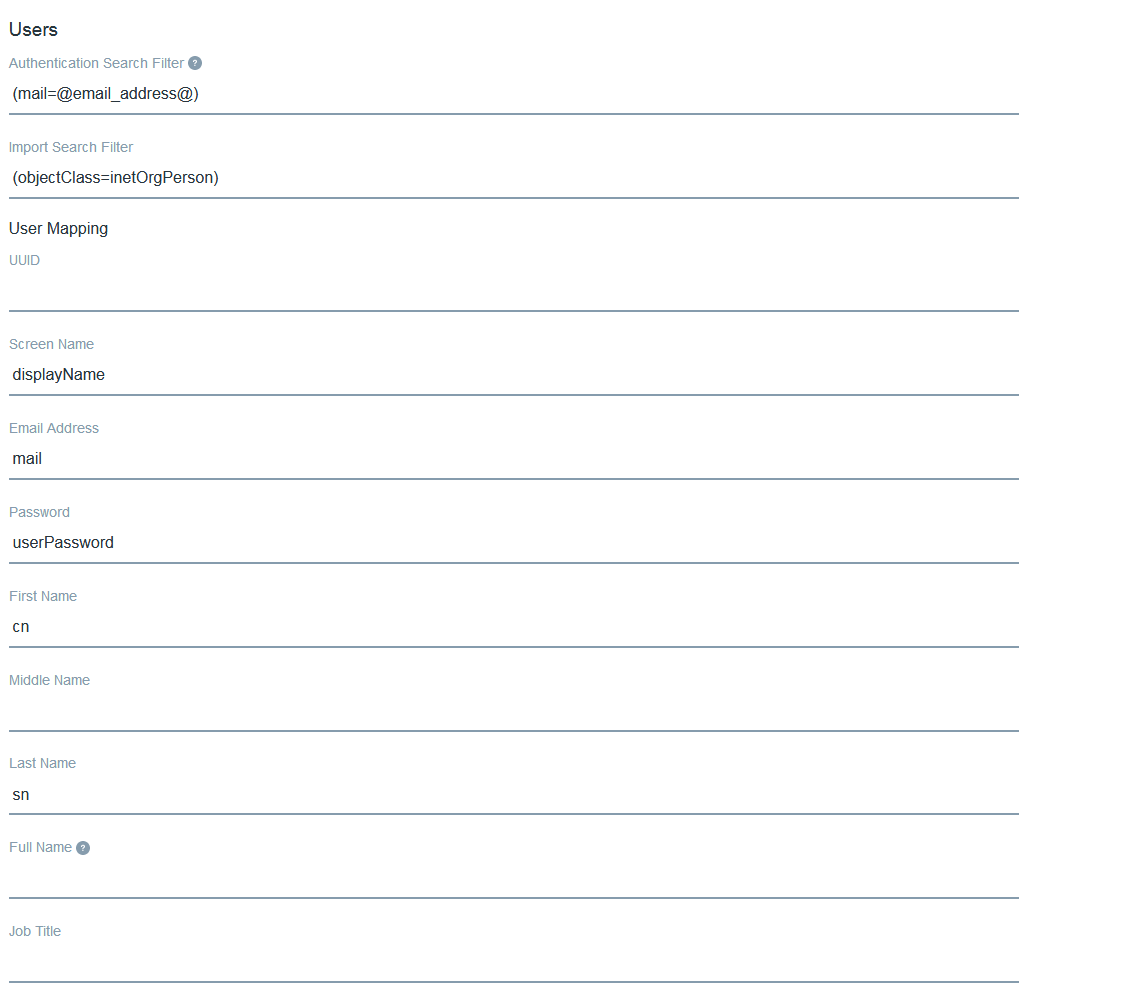
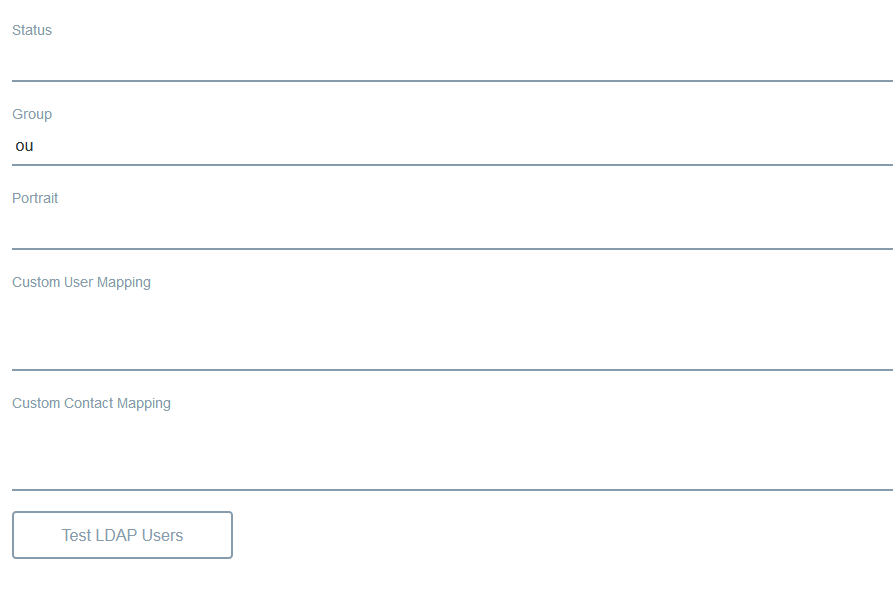
Below is a screenshot of User Structure in OpenLDAP.
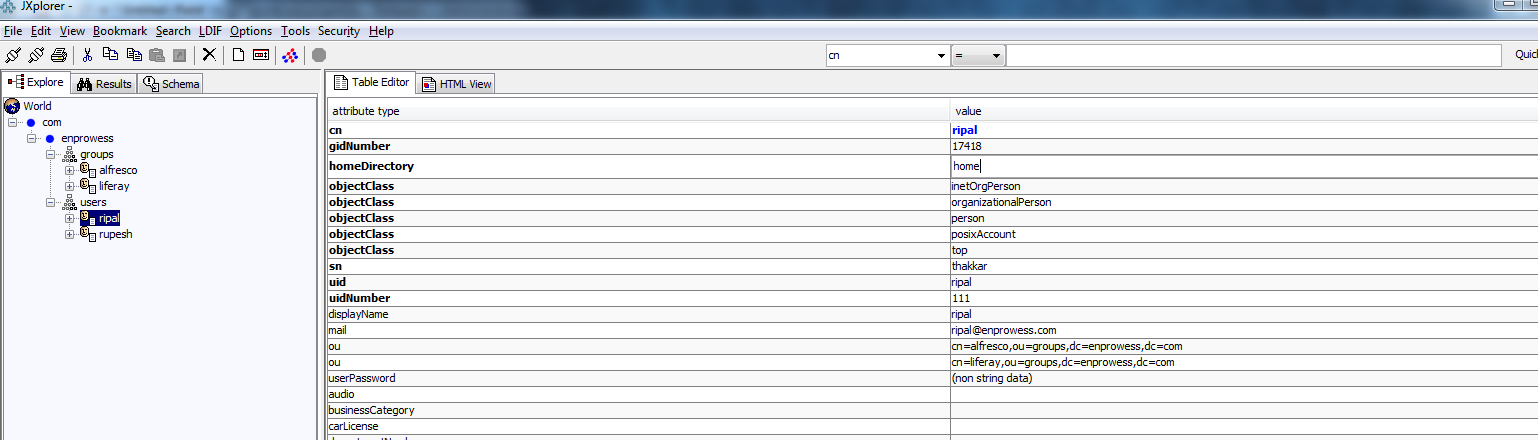
- “Ou” user attribute that contains information about one or multiple groups that user is associated. This is used to identify/import groups that associated with the user.
Clicking on “Test LDAP Users” button will fetch & list down ldap users in Popup as below.
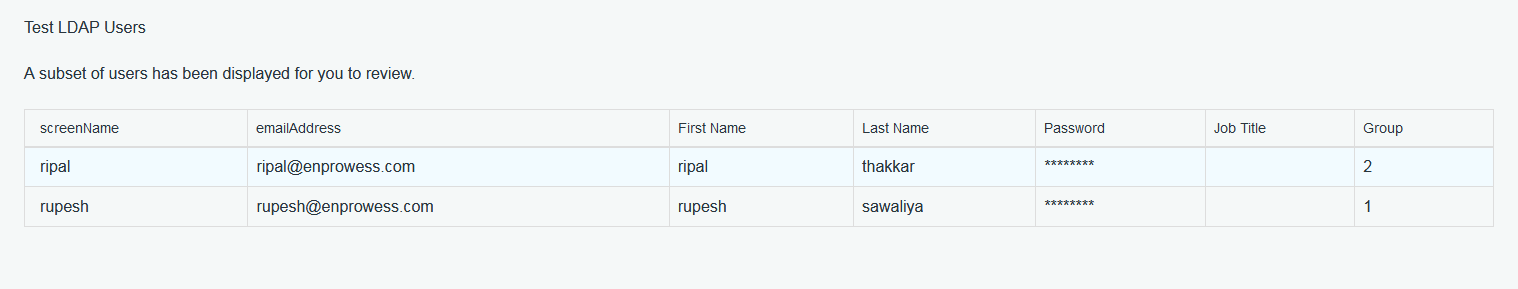
Now, Let’s configure Group details as seen below.

Below is a screenshot of Group Structure in OpenLDAP.
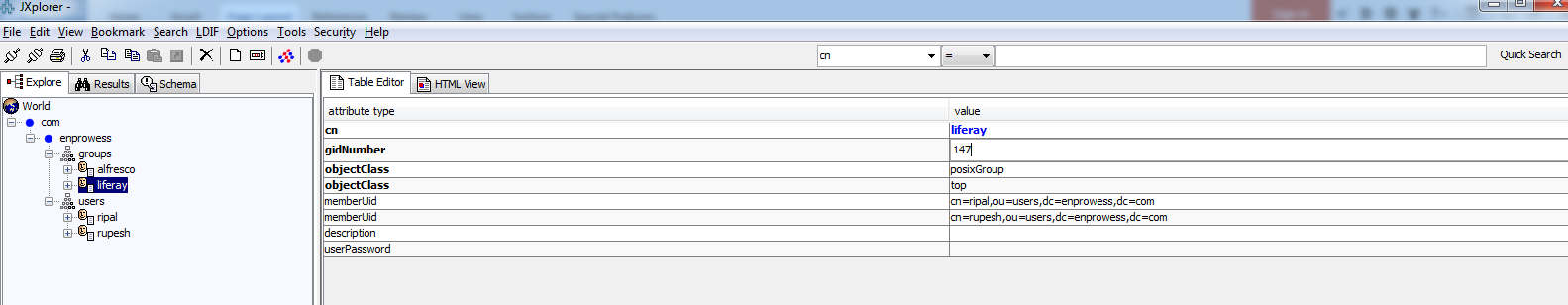
- “memberUid” group attribute has details of users associated. It is an attribute of “PosixGroup” objectClass. This is used to identify/import users that associated with the group.
Clicking on Test LDAP Groups button will show groups available in LDAP in Popup as below.

Export Settings can be configured as below if In case Exporting User details from Liferay to LDAP Server is needed.
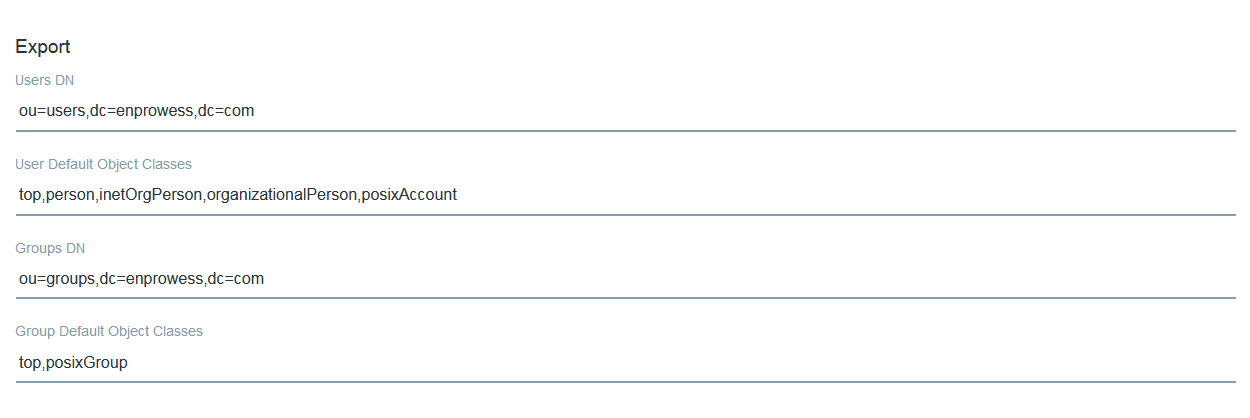
Clicking On SAVE button will show list of configured LDAP servers.
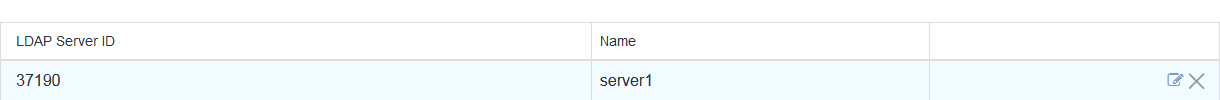
Let’s now do other setting that are required for import/authentication.
Check “enabled” box to enable LDAP authentication.
Check “required” if authentication against LDAP is required. This will mandate user to get validated against LDAP first before log in to Liferay Portal.
- Note: In case of users with no LDAP accounts, keep this box UnChecked.
Select “Bind” as Method to start an user session.
Select password algorithm that is used to encrypt passwords in LDAP. This needs to be set only if Method is set to “Password Compare” previously.
Here is a screenshot of these settings.

Under the Import/Export Section check “Enable Import” to import users in bulk. Check “Enable Import on Startup” further to import users at server startup otherwise a scheduler will run at a particular time period to perform bulk user import. Keep “Enable Import” unchecked to import user at the time of login.
Set Import interval as per requirement if ‘User Import Scheduler’ is required to run.
Keep import method as User which will import the user first and then will import groups that an user is associated to in LDAP.
- Selecting import method as Group will do vice versa meaning import will be performed for a particular group first and then for users associated to group.
Keep “Import User Strategy” as “Auth Type” if “Required” option is checked as shown previously.
Check “Enable User Password on Import ” if changing a password is required at the time of first login.
Check “Auto generate User password” if it is required to auto generate password for an user else system will ask user to enter new password.
Provide Default password that needs to be set by default if “Auto generate User password” is checked.
Checking “Enable Group Cache on Import” will look up for a group object in cache first before importing from LDAP.
Checking “Create Role per Group on Import” will create role for a group imported and assign it to associated users. This will give associated users same permissions that is assigned to an userGroup created in liferay, by import, for LDAP group.
Check “Enable Export” if Exporting is required from Liferay to LDAPServer.
Check “Enable Group Export” to enable export for group details changes.
Check “Use LDAP Password policy ” to ask liferay to use Password Policy that is set to LDAP else liferay will use its local Policy that is defined in Control Panel > Configuration > Service Access policy.
Below is a reference Screenshot.


Click on Save.
Now, Logging in with LDAP User results into Creation of User and UserGroup and UserGroupRole into Liferay. Below is a sequence of screen shots that shows such creation after user logs in first time.
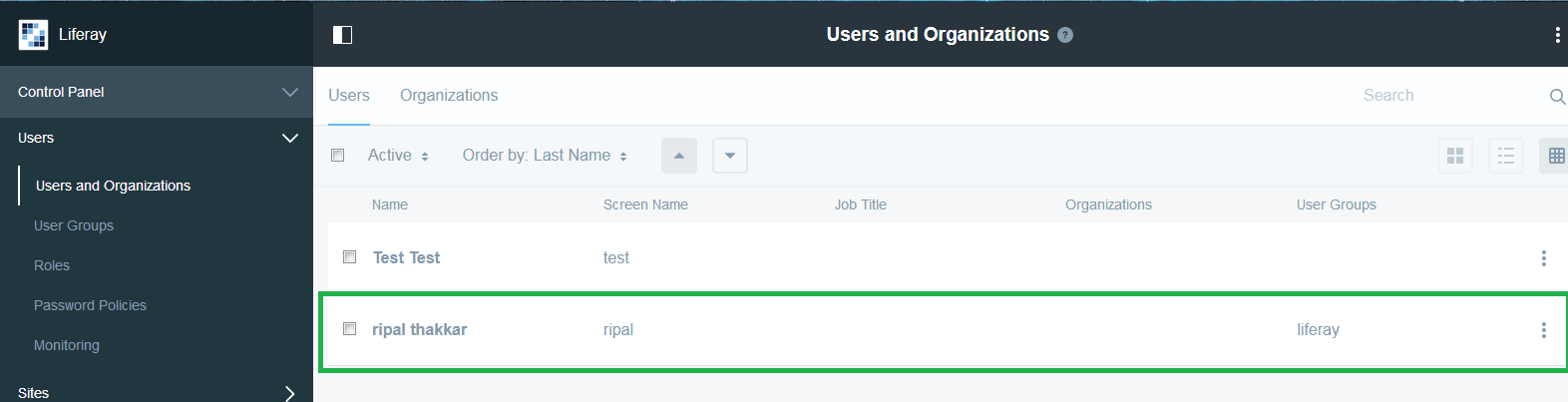
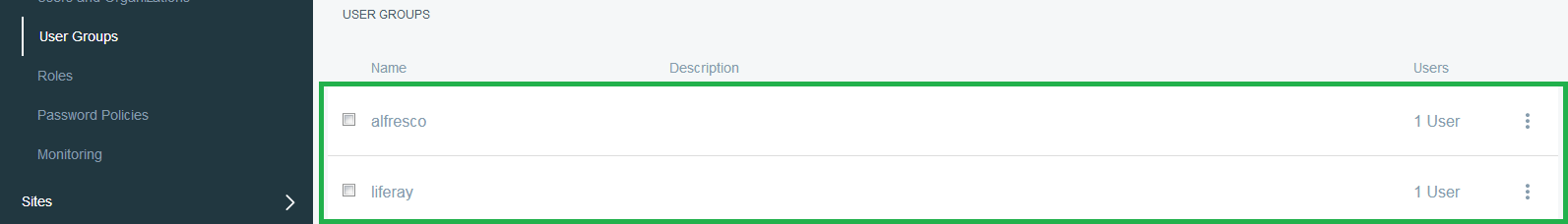
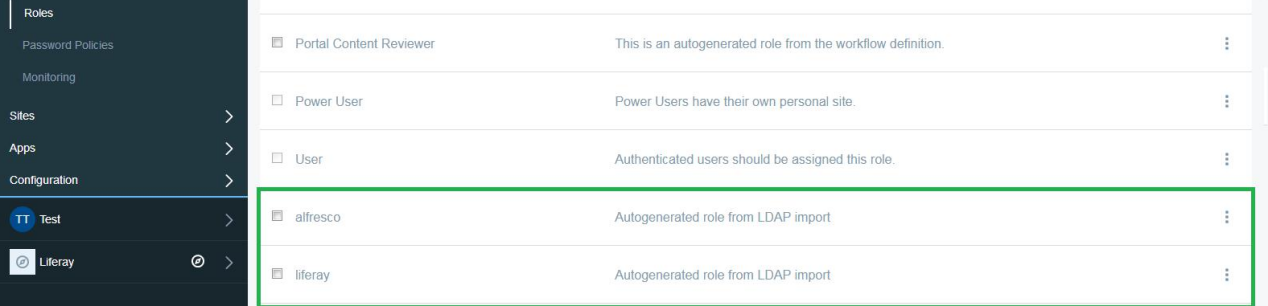
Note:-Below are the properties that can be used to do configuration in portal-ext.properties in other versions of Liferay prior to 7.
#LDAP Configuration
ldap.auth.enabled=true
ldap.auth.required=true
ldap.import.enabled=true
ldap.import.interval=-5
auth.pipeline.pre=com.liferay.portal.security.auth.LDAPAuth
ldap.auth.password.encryption.algorithm=MD5
ldap.import.create.role.per.group=true
ldap.base.provider.url.0=ldap://etpl007:389
ldap.base.dn.0=dc=enprowess,dc=com
ldap.security.principal.0=cn=Manager,dc=enprowess,dc=com
ldap.security.credentials.0=secret
ldap.auth.search.filter.0=(mail=@email_address@)
ldap.users.dn.0=ou=users,dc=enprowess,dc=com
ldap.user.mappings.0=emailAddress=mail\nscreenName=displayName\npassword=userPassword\nfirstName=cn\nlastName=sn\ngroup=ou
ldap.user.default.object.classes.0=top,inetOrgPerson,organizationalPerson,person,posixAccount
ldap.import.user.search.filter.0=(objectClass=inetOrgPerson)
ldap.import.group.search.filter.enabled=false
ldap.import.method=user
ldap.groups.dn.0=ou=groups,dc=enprowess,dc=com
ldap.group.mappings.0=groupName=cn\ndescription=description\nuser=memberUid
ldap.group.default.object.classes.0=top,posixGroup
ldap.import.group.search.filter.0=(objectClass=posixGroup)
Post By,
Ripal Thakkar